Please download and install the Tor Browser to ensure anonymity:
Use this link to visit the WildLeaks secure server with the Tor Browser: http://n7kt2meojoykkp6udjxzofctxextpmp2zo533hzzdwdhv43p4r3ef3ad.onion/#/
WildLeaks has implemented a very secure Tor-based online platform in order to allow our sources to stay anonymous and to submit ‘sensitive’ information in the most secure way possible, always encrypted, in respect to data transmission and management.
ANONYMOUS AND SECURE
You will be using a submission system that is entirely based on the use of Tor technology, which is already integrated into our platform using the software provided by our partners GlobaLeaks.
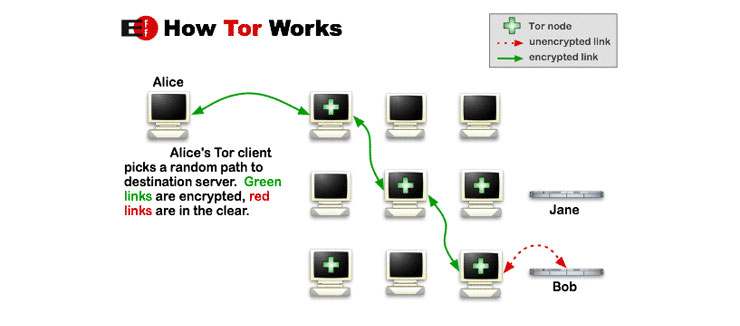
Tortechnology allows people to navigate the Internet anonymously. It is made up of a chain of proxies that work to hide the users’ original IP address (your Internet identity). It is considered the best technology for digital anonymity available to Internet users and academics. IT security experts constantly revise the software to ensure anonymity.
In order to remain anonymous and untraceable, we recommend that instead of your usual Browser (Safari, Chrome, Firefox, etc.) you use the Tor Browser (click here for more information and for an easy download of the Tor Browser Bundle).
IMPORTANT: After you download and open the Tor Browser, if you want to submit information and tips to WildLeaks, click on the big orange button on our homepage or copy and paste the following WildLeaks’ Tor Hidden Service Address into the Tor Browser: http://n7kt2meojoykkp6udjxzofctxextpmp2zo533hzzdwdhv43p4r3ef3ad.onion/#/
Whether or not anonymity is important to you, Tor can also be useful as a secure means of promoting Internet freedom, and circumventing censorship and electronic restrictions so that you may access or publish blogs and news reports anonymously.
Tor guarantees that no personal traces remain in WildLeaks systems.
Other Options for Submitting Information Securely & Anonymously
For whistleblowers that are unable to utilize the WildLeaks platform, WildLeaks offers alternative methods to submit reports as confidentially as possible. These include the following:
1. Set up an anonymous encrypted email service using ProtonMail.ch and then send us an email to: wildleaks@protonmail.ch
2. Use Threema, a versatile app for your smartphones that encrypts all your communications end-to-end including messages, group chats, files and even status messages.
A phone number or email address is NOT required to use Threema, a unique feature that allows the Threema user to be completely anonymous. After the app has been installed, in order to connect to WildLeaks anonymously just send your Threema ID to wildleaks@protonmail.ch, and a WildLeaks representative will get back to you from the organization’s Threema account.




