WildLeaks has implemented a Tor-based secure platform in order to allow our sources to stay anonymous and to submit sensitive information in the most secure way possible, always encrypted, in respect to data transmission and management.
Anonymous and Secure
If you have concerns about your traceability and you choose to submit your information in total anonymity, you will be using a submission system that is entirely based on the use of Tor technology, which is already integrated into our platform. Thus, as a whistleblower, in order to protect your anonymity, you must first download and install the Tor Browser. It is very easy and similar to using a normal browser:
- Download the Tor Browser here.
- Execute the file you downloaded to extract the Tor Browser into a folder on your computer (or pendrive).
- Then simply open the folder and click to start Tor Browser.
- To make an anonymous submission to WildLeaks, copy and paste into the Tor Browser the WildLeaks’ Tor Hidden Service Address: http://n7kt2meojoykkp6udjxzofctxextpmp2zo533hzzdwdhv43p4r3ef3ad.onion/#/

The Tor homepage
The Tor Browser lets you use Tor on Windows, Mac OS X, or Linux without needing to install any software. It can run off a USB flash drive, comes with a pre-configured web browser to protect your anonymity, and is self-contained.
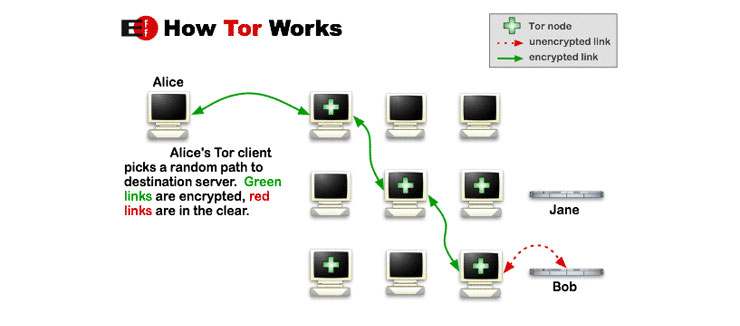
Tor technology protects you by bouncing your communications around a distributed network of relays run by volunteers all around the world. It prevents somebody watching your Internet connection from learning what sites you visit, it prevents the sites you visit from learning your physical location, and it lets you access internet sites that are blocked.